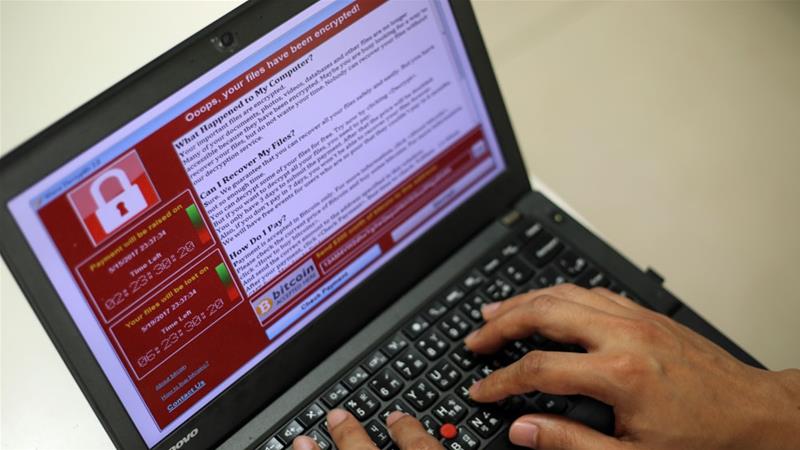
By now, many netizens of the world have heard of the notorious WannaCry virus. It’s part of a piece of code called Ransomware (which says everything you need to know about it).
For the three people reading this who might need a bit more context, WannaCry infests your computer either because you opened an infected email or message link, or were infected from other computers on your network (this could even mean just people who are using the same WiFi as you). The hackers are now in control of your computer and will block access to it until you pay them a ransom.
WannaCry will ask for USD300 paid in BitCoin, which will go up to USD600 if not paid in time. Another timer will count down until all of your files are gone forever.
However, we’ve heard personal reports that since these hackers are criminals, they are not obligated to release your files once you’ve made payments. In fact, a victim of a previous Ransomware attack told us that the hackers kept asking for more money once he paid, until he eventually stopped and lost all of his data and also cash. He never got anything on his computer back either.
Since WannaCry has now definitively hit at least two local businesses right here in Malaysia, it’s important to remember that prevention is better than cure. So, here are some steps to take and the links you’ll need to protect yourself.
1. Keep Windows Updated
WannaCry only attacks Windows thanks to a flaw in the Windows system that has been patched. So, good news for users of Windows 8.1 and above. (like Windows 10). If you’ve updated your device since March, then you’re safe from WannaCry. This is also a gentle reminder for users to update your device if you haven’t.
If your system is already supported, just install your relevant updates as instructed, especially if you’ve been disabling your updates. Supported systems include: Windows Vista, Windows Server 2008, Windows 7, Windows Server 2008 R2, Windows 8.1, Windows Server 2012, Windows 10, Windows Server 2012 R2 and Windows Server 2016.
But not everyone is up to the tech curve. And since many companies still use defunct systems like Windows XP or Windows 2003, the devs behind the brand have also released patches for these systems, downloadable below:
- Companies who haven’t applied to Windows to update their servers can do so here.
- For those with personal Windows systems, you can find the relevant links here.
2. Back Up Your Files
If you haven’t been infected by WannaCry, now is your chance to start backing up your files. If you want to backup your files using Windows:
Step 1: Click the Start button.
Step 2: Go to Control Panel, then System and Maintenance, and find Backup and Restore.
Step 3: You can either:
- Set up backup if you haven’t backed up your computer before
- Back up now if you have backed up before.
- Create new, full backup if you want to create a new backup.
Step 4: Choose the files you want to backup
- This definitely includes anything you’ll miss if your computer gets locked by WannaCry. All of your personal documents, precious photos and work-related files should be of top-priority for backups.
But for a fuller and more comprehensive backup, you can choose to use commercial backup softwares.
Free Backup Software:
Paid Backup Software:
Or you can opt for a cloud-based backup software like Carbonite. There are also manual cloud-based services that you can use to store your files on, such as Google Drive, OneDrive and Dropbox.
3. Get Your Antivirus Game On
Now that WannaCry has turned into an epidemic, many antivirus companies now include WannaCry into their database. If you have an antivirus, keep it updated to the latest version (this can be done within your antivirus programs) then do the following:
Step 1: Do a manual scan of all your files.
Step 2: If you see MEM:Trojan.Win64.EquationDrug.gen, remove it.
Step 3: Reboot your computer.
Step 4: Make sure your Antivirus continuously scans your computer.
Well-known antivirus software:
4. Disable The Server Message Block (SMB)
The SMB is primarily used to provide shared access to files, printers, serial ports and other communications within a network.
In a simple explanation, WannaCry exploits flaws in the SMB Server.
To disable it, first search for “Windows features”. Click on “Turn Windows features on or off”.
Scroll to find the SMB 1.0/CIFS File Sharing Support and uncheck it. Press “OK” and then restart your computer.
What To Do If You’re Infected?
First of all: I’m sorry.
Best thing you can do is to not pay the fine. There’s no guarantee that you’ll even get your files back, and this will just encourage more of these worms to pop up.
Your chances of regaining all of your files are currently slim, but we found some pages online that might help you recover your files. However, we just want to say that we’ve never personally tried these methods, so proceed with caution. If done wrong, you might even damage your computer files or systems.
- This is a step-by-step guide on how to remove WannaCry, with step 1 being ‘Enter your computer’s safe mode’.
- Microsoft recommends that you disable SMBv1, SMBv2, and SMBv3 in Windows and Windows Servers to protect your non-updated computers from the loophole that WannaCry is attacking. Here’s how.
But the best protection measure is to NEVER OPEN DODGY EMAILS, OR CLICK ON SUSPICIOUS DOWNLOAD LINKS. This rule applies no matter what you do online.
Good luck, and hope this helps you a little.
Feature Image Credit: Al Jazeera