Who doesn’t have a Google account? Youtube, Gmail, Drive, Workspace, Analytics, Ads… the list goes on—all are tied to a single account that links back to you.
And you would be forgiven for thinking that one of the largest tech giants in the world is making sure that billions of phone numbers of its users are protected behind impervious cybersecurity barriers.
Alas, every wall appears to have a crack, and one was just found by a cybersecurity researcher under the alias Brutecat, who identified fairly simple vulnerabilities that allowed him to uncover phone numbers tied to every Google account there is.
As is usually the case in complex systems, there are interdependencies that someone failed to spot and seal at the right time.
It all started with Google’s username recovery page, which functioned even with JavaScript disabled, at which point it lacked sufficient anti-bot protection (which relied on JavaScript). In essence, it could then be spammed with harmful requests at a very high rate.
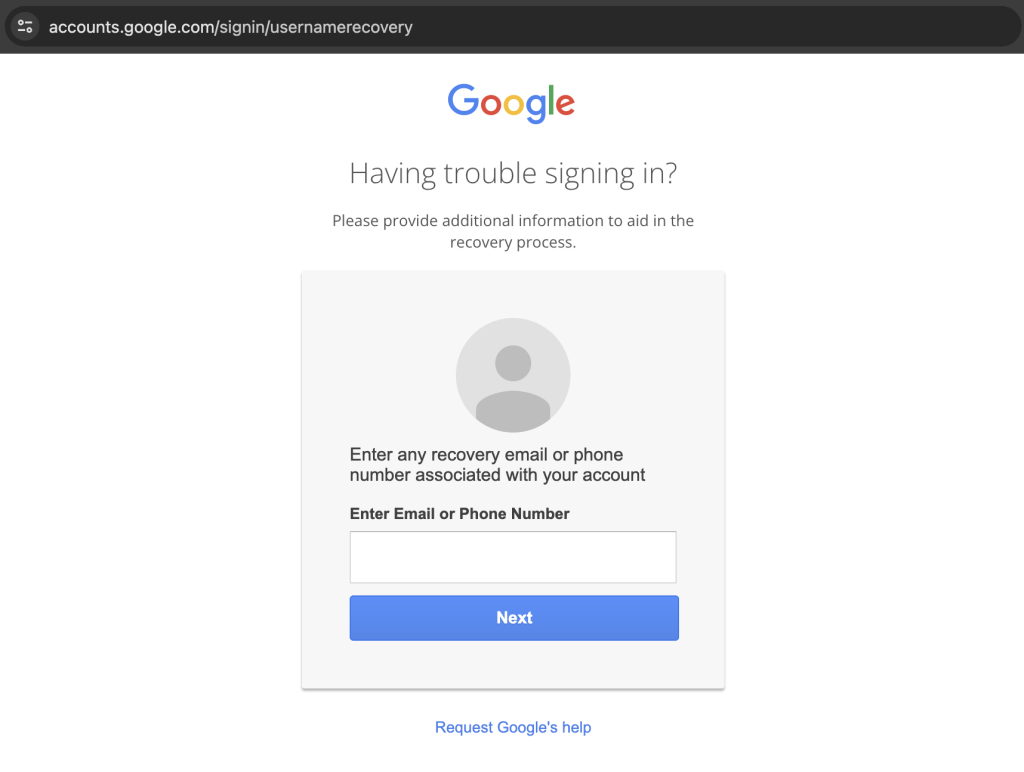
A weakness in the form itself allowed you to check back if a particular name is associated with a given email or phone number, and as you may have noticed if ever trying to recover your account, Google provides the last two digits of your phone number as a hint.
Depending on the country, the total number of digits is different, providing more or fewer combinations that an automated bot could spam the recovery form with before making a match.
Using a US$0.30 per hour server, Brutecat was able to initiate 40,000 checks per second using the compromised form and determine how much time it would take to match a phone number to a name in different countries.
Singapore, with its 8-digit phone numbers, did not fare well.
Theoretically 8 digits provide tens of millions of combinations. However, if you know the last two from Google’s hint, then that cuts it down to just a few hundred thousand. Moreover, mobile numbers in Singapore start with either 8 or 9, reducing it further to at most 200,000 possibilities. Divide that by 40,000 requests every second and you get 5 seconds.
| Country code | Time required |
|---|---|
| United States (+1) | 20 mins |
| United Kingdom (+44) | 4 mins |
| Netherlands (+31) | 15 secs |
| Singapore (+65) | 5 secs |
The exploit could be used in two ways.
First, with additional vulnerability in Looker Studio (a data tool by Google), any account could be added as an owner to any document created on the platform, revealing the user’s name even if they didn’t approve it. That’s how you could connect the email to a name and subsequently use it to discover the phone number.
But you could also harvest many numbers in a single attempt, as the form would spit back out phone details of people who matched only some criteria, like first and/or last name.
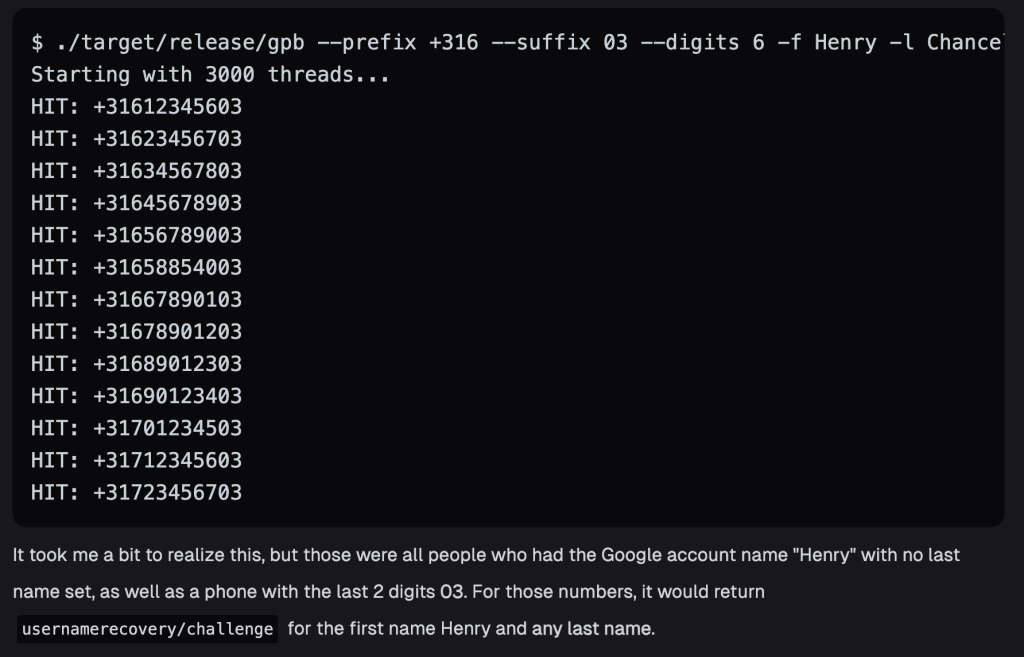
So, if your only intent was to collect large quantities of phone numbers of verified Google users, you could have easily done that as well.
While Singaporeans were particularly vulnerable, given that their information could have been compromised in a matter of seconds (as opposed to many minutes, like in the US, which could make it uneconomical to collect too much information for too many people at once), if you were specifically targeted, then your data could easily have been extracted no matter where you’re from.
Fortunately, while we can’t say for sure if anybody else has figured this out and secretly used it to extract personal details, it doesn’t seem that a massive breach had happened before Google patched the loophole last month and rewarded the ethical hacker with S$5,000 for the effort.
It was a close call, though.
- Read other articles we’ve written on tech giants here.
Featured Image Credit: photogearch/ depositphotos










